Compare commits
27 Commits
f44e5a44d6
...
master
| Author | SHA1 | Date | |
|---|---|---|---|
| 1572aabe53 | |||
| 7346be9df6 | |||
| 6b254cc1d7 | |||
| 290736a056 | |||
| 87b7db4235 | |||
| ddcb565e2f | |||
| a247c7edd6 | |||
| 221c7339e2 | |||
| 41be82c923 | |||
| a0cdaf5428 | |||
| 23289409a8 | |||
| 66dde247d7 | |||
| 9fa52aec35 | |||
| fe46e4cc7e | |||
| 4a871cbdd4 | |||
| 0e77d19135 | |||
| 894819c9d1 | |||
| f1fdfdb1e5 | |||
| 695f0876f0 | |||
| f613911819 | |||
| 1474f15660 | |||
| 2b4cc6353b | |||
| d8eef073c8 | |||
| c077f23e9f | |||
| 60e47d959b | |||
| fa840c3c9f | |||
| 15557de239 |
49
Archguide.md
49
Archguide.md
@ -2,7 +2,7 @@
|
|||||||
title: Arch Linux Install guide
|
title: Arch Linux Install guide
|
||||||
description:
|
description:
|
||||||
published: true
|
published: true
|
||||||
date: 2019-11-06T00:04:52.555Z
|
date: 2020-03-19T05:25:06.772Z
|
||||||
tags:
|
tags:
|
||||||
---
|
---
|
||||||
|
|
||||||
@ -94,24 +94,7 @@ options root=/dev/sda2 rw
|
|||||||
|
|
||||||
However, don't reboot just yet. There are still some things to do before getting into a properly running system.
|
However, don't reboot just yet. There are still some things to do before getting into a properly running system.
|
||||||
|
|
||||||
While we are in the subject of the kernel options cmdline, let's enter...
|
There is a [big caveat](https://doc.fosc.space/Archguide#the-partuuid-dilemma) here which is good to read.
|
||||||
|
|
||||||
|
|
||||||
#### The PARTUUID dilemma
|
|
||||||
> Using partition names to boot instead of their unique indetifiers will cause the OS not to boot if (when) the partition count or disk order of the computer changes.
|
|
||||||
> It may change even across reboots. To avoid this issue, extract your partition's `PARTUUID` using `blkid` and edit your options line accordingly.
|
|
||||||
{.is-danger}
|
|
||||||
|
|
||||||
```
|
|
||||||
title Arch Linux
|
|
||||||
linux /vmlinuz-linux
|
|
||||||
initrd /initramfs-linux.img
|
|
||||||
options root=PARTUUID="9b505600-2d6a-3660-b0c3-d2dfd653c5fd" rw
|
|
||||||
```
|
|
||||||
|
|
||||||
> As long as your firmware doesn't change disk order randomly, **and you know what to touch if it breaks**, this step can be done later.
|
|
||||||
{.is-info}
|
|
||||||
|
|
||||||
|
|
||||||
## Configuring the system so it's usable
|
## Configuring the system so it's usable
|
||||||
### Language
|
### Language
|
||||||
@ -146,8 +129,6 @@ reboot
|
|||||||
```
|
```
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
# btw I use arch
|
# btw I use arch
|
||||||
*but it sucks, blackscreens and lasts 5 minutes on battery*
|
*but it sucks, blackscreens and lasts 5 minutes on battery*
|
||||||
|
|
||||||
@ -166,7 +147,7 @@ timedatectl set-ntp true
|
|||||||
## I forgot to install a terminal emulator
|
## I forgot to install a terminal emulator
|
||||||
You always have the TTYs.
|
You always have the TTYs.
|
||||||
|
|
||||||
Press `ctrl+alt+F4` and login normally.
|
Press <kbd>ctrl</kbd>+<kbd>alt</kbd>+<kbd>F4</kbd> and login normally.
|
||||||
|
|
||||||
## Package management
|
## Package management
|
||||||
Read the [pacman rosetta](https://wiki.archlinux.org/index.php/Pacman/Rosetta).
|
Read the [pacman rosetta](https://wiki.archlinux.org/index.php/Pacman/Rosetta).
|
||||||
@ -202,14 +183,31 @@ Change to high quality audio profile to not **instantly die** upon music playbac
|
|||||||
|
|
||||||
## Battery life is nonexistent
|
## Battery life is nonexistent
|
||||||
The TLP daemon tunes tunables inside the heavily tunable Linux kernel so you have a semblance of battery life.
|
The TLP daemon tunes tunables inside the heavily tunable Linux kernel so you have a semblance of battery life.
|
||||||
|
You can also install it in normal desktops and it makes some difference in wall power draw.
|
||||||
|
|
||||||
|
|
||||||
Install `tlp` and enable it, which is quirky.
|
Install `tlp` and enable it, which is quirky.
|
||||||
```
|
```
|
||||||
systemctl enable --now tlp tlp-sleep
|
systemctl enable --now tlp
|
||||||
systemctl mask systemd-rfkill.socket
|
systemctl mask systemd-rfkill systemd-rfkill.socket
|
||||||
```
|
```
|
||||||
|
|
||||||
You can technically also install it in normal desktops and it makes some difference in wall power draw.
|
## The PARTUUID dilemma
|
||||||
|
> Using partition names to boot instead of their unique identifiers will cause the OS not to boot if (when) the partition count or disk order of the computer changes.
|
||||||
|
> It may change even across reboots. To avoid this issue, extract your partition's `PARTUUID` using `blkid` and edit your options line accordingly.
|
||||||
|
{.is-danger}
|
||||||
|
|
||||||
|
```
|
||||||
|
title Arch Linux
|
||||||
|
linux /vmlinuz-linux
|
||||||
|
initrd /initramfs-linux.img
|
||||||
|
options root=PARTUUID="9b505600-2d6a-3660-b0c3-d2dfd653c5fd" rw
|
||||||
|
```
|
||||||
|
|
||||||
|
> As long as your firmware doesn't change disk order randomly, **and you know what to touch if it breaks**, you can ignore this.
|
||||||
|
>
|
||||||
|
> *For now.*
|
||||||
|
{.is-info}
|
||||||
|
|
||||||
## NVIDIA Optimus
|
## NVIDIA Optimus
|
||||||
Install `nvidia` and `nvidia-utils` as normal.
|
Install `nvidia` and `nvidia-utils` as normal.
|
||||||
@ -238,4 +236,3 @@ More information [can be found at the usual place](https://wiki.archlinux.org/in
|
|||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
BIN
best_logo.png
Normal file
BIN
best_logo.png
Normal file
Binary file not shown.
|
After Width: | Height: | Size: 114 KiB |
@ -2,7 +2,7 @@
|
|||||||
title: PlutoSDR
|
title: PlutoSDR
|
||||||
description: Primeros pasos con el PlutoSDR
|
description: Primeros pasos con el PlutoSDR
|
||||||
published: true
|
published: true
|
||||||
date: 2019-06-19T20:14:02.288Z
|
date: 2020-04-19T03:27:22.422Z
|
||||||
tags:
|
tags:
|
||||||
---
|
---
|
||||||
|
|
||||||
153
es/traefik.md
Normal file
153
es/traefik.md
Normal file
@ -0,0 +1,153 @@
|
|||||||
|
---
|
||||||
|
title: Traefik v2
|
||||||
|
description: Routing seguro para tus aplicaciones en containers usando Traefik v2 con Let's Encrypt
|
||||||
|
published: true
|
||||||
|
date: 2020-04-19T03:25:17.168Z
|
||||||
|
tags:
|
||||||
|
---
|
||||||
|
|
||||||
|
# Configurar traefik v2 para routing seguro como proxy reverso con HTTPS
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
## Introducción
|
||||||
|
|
||||||
|
Una configuración robusta de proxy inverso es crítica para cualquier configuración selfhosted que tenga elementos expuestos a través de internet. Si bien los servicios de proxy inverso se utilizan a menudo por razones de equilibrio de carga y seguridad, la mayoría de los propietarios de servidores domésticos los utilizan para enrutar las solicitudes dirigidas a diferentes dominios o subdominios a diferentes hosts o servicios internos. En mi caso puedes ver todos mis servicios en https://server.crstian.me/.
|
||||||
|
|
||||||
|
En esto post vamos a ver como configurar Traefik como proxy inverso como por ejemplo [NGINX](https://www.nginx.com/).
|
||||||
|
|
||||||
|
Vamos a ver como hacer routing de forma segura a peticiones dirigidas a un subdominio que apunte a un puero específico de un container, todo ello a través de forma segura mediante HTTPS.
|
||||||
|
|
||||||
|
## ¿Qué es un proxy inverso?
|
||||||
|
|
||||||
|
Un proxy inverso es un tipo de servidor proxy que recupera recursos en nombre de un cliente desde uno o más servidores. Estos recursos son entonces regresados al cliente como si se originaran en el propio servidor Web.
|
||||||
|
|
||||||
|
Lo que explicado de una forma más vulgar sería en nuestro caso acceder a distintos servicios que tenemos de forma local pero desde el exterior y que en este caso Traefik haga el trabajo de routing y dependiendo el subdominio nos lleve a un servicio u otro.
|
||||||
|
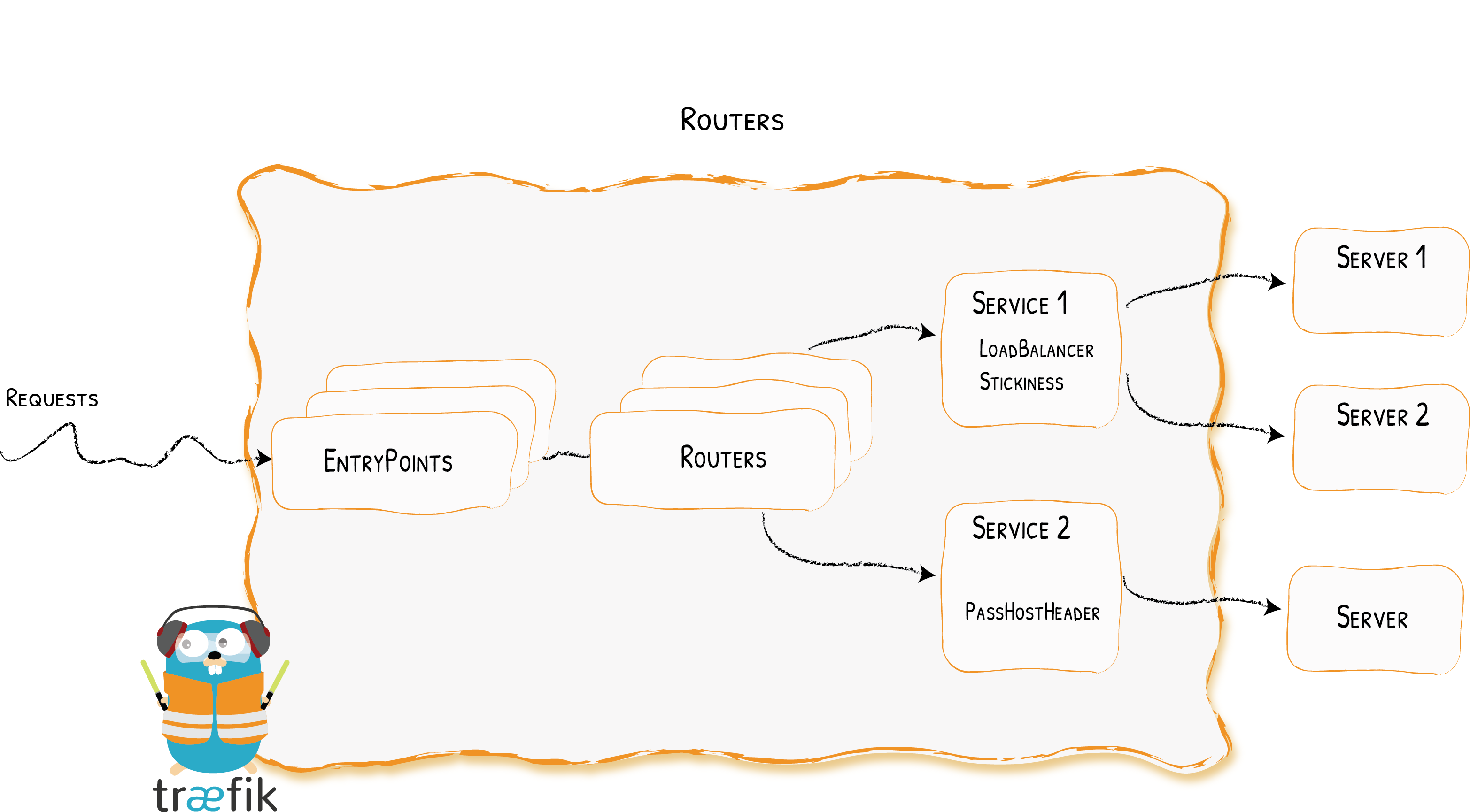
|
||||||
|
|
||||||
|
### Balanceo de carga
|
||||||
|
|
||||||
|
Un proxy inverso puede distribuir la carga de solicitudes entrantes a varios servidores, con cada servidor ejecutando su propia área de aplicación.
|
||||||
|
|
||||||
|
Los proxies inversos proporcionan una capa adicional de seguridad al no revelar nunca la dirección IP del servidor backend que realmente maneja las solicitudes. Esto significa que los atacantes normalmente sólo podrán atacar a los propios servidores proxy inversos.
|
||||||
|
|
||||||
|
### Encriptación SSL
|
||||||
|
|
||||||
|
Un proxy inverso lo podemos configurar con encriptación SSL para poder generar certificados automaticamente para cada ruta con [Let's Encrypt](https://letsencrypt.org/es/).
|
||||||
|
|
||||||
|
## Configurar Traefik v2
|
||||||
|
|
||||||
|
En nuestro caso vamos a levantarlo con un [docker-compose.yml](https://docs.docker.com/compose/)
|
||||||
|
|
||||||
|
```
|
||||||
|
version: '3.7'
|
||||||
|
|
||||||
|
services:
|
||||||
|
traefik:
|
||||||
|
image: traefik:latest
|
||||||
|
network_mode: host
|
||||||
|
volumes:
|
||||||
|
- ./config/:/etc/traefik/
|
||||||
|
- /var/run/docker.sock:/var/run/docker.sock
|
||||||
|
```
|
||||||
|
Ahora vamos a configurar Traefik con su archivo de configuración traefik.toml.
|
||||||
|
|
||||||
|
```
|
||||||
|
api:
|
||||||
|
dashboard: true
|
||||||
|
|
||||||
|
entryPoints:
|
||||||
|
web:
|
||||||
|
address: ":80"
|
||||||
|
web-secure:
|
||||||
|
address: ":443"
|
||||||
|
|
||||||
|
providers:
|
||||||
|
docker:
|
||||||
|
endpoint: "unix:///var/run/docker.sock"
|
||||||
|
exposedByDefault: false
|
||||||
|
file:
|
||||||
|
filename: /etc/traefik/config.yml
|
||||||
|
watch: true
|
||||||
|
|
||||||
|
certificatesResolvers:
|
||||||
|
default:
|
||||||
|
acme:
|
||||||
|
email: your email
|
||||||
|
storage: /etc/traefik/acme/acme.json
|
||||||
|
tlsChallenge: {}
|
||||||
|
```
|
||||||
|
|
||||||
|
### Integración con Docker
|
||||||
|
|
||||||
|
Traefik utiliza la API de cada [proveedor](https://docs.traefik.io/providers/overview/) para encontrar información de routing y configurarse en función a ello.
|
||||||
|
|
||||||
|
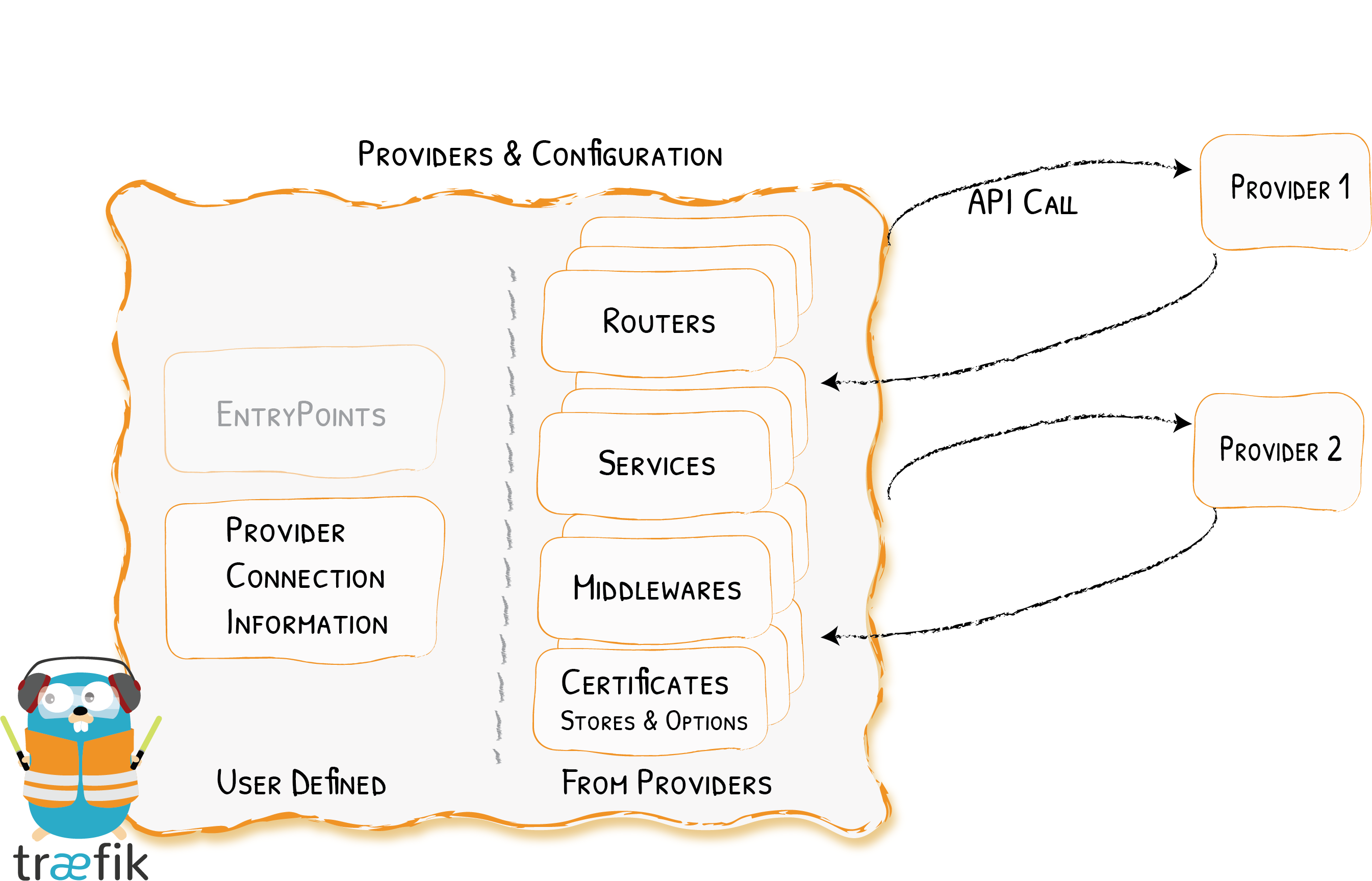
|
||||||
|
|
||||||
|
### Puntos de entrada
|
||||||
|
|
||||||
|
Los puntos de entrada simplemente definen los puertos en los que Traefik escuchará para recibir los paquetes. Aquí se configuran dos puntos de entrada, web y websecure para los puertos 80 y 443.
|
||||||
|
|
||||||
|
## Configuración de los containers
|
||||||
|
|
||||||
|
El último paso para exponer nuestro container usando Traefik es añadir algunas etiquetas Docker que permitirán a Traefik encontrarlo.
|
||||||
|
|
||||||
|
Estas son las etiquetas necesarias:
|
||||||
|
|
||||||
|
```
|
||||||
|
labels:
|
||||||
|
- traefik.enable=true
|
||||||
|
- traefik.http.routers.yourservicename.entryPoints=web-secure
|
||||||
|
- traefik.http.routers.yourservicename.rule=Host(`subdomain.your.domain`)
|
||||||
|
- traefik.http.routers.yourservicename.tls=true
|
||||||
|
- traefik.http.routers.yourservicename.middlewares=user:password
|
||||||
|
- traefik.http.services.yourservicename.loadbalancer.server.port=serviceport
|
||||||
|
```
|
||||||
|
- `yourservicename` tenemos que cambiarlo por el nombre de nuestra aplicación, por ejemplo `netdata`
|
||||||
|
|
||||||
|
- `subdomain.your.domain` tenemos que cambiarlo por nuestro subdominio que queremos que apunte a nuestra aplicación, por ejemplo `netdata.crstian.me`
|
||||||
|
|
||||||
|
- `serviceport` aquí tenemos que cambiarlo por el puerto que use nuestro servicio
|
||||||
|
|
||||||
|
- `user:password` en caso de que queramos ponerle usuario y contraseña para entrar a ese servicio debemos usar usuario y contraseña como si fuera htaccess
|
||||||
|
|
||||||
|
|
||||||
|
Un ejemplo de un servicio que tengo corriendo en mi servidor con su docker-compose.yml
|
||||||
|
|
||||||
|
```
|
||||||
|
version: '3'
|
||||||
|
services:
|
||||||
|
caddy:
|
||||||
|
image: abiosoft/caddy
|
||||||
|
volumes:
|
||||||
|
- '/storage/shared:/srv'
|
||||||
|
labels:
|
||||||
|
- traefik.enable=true
|
||||||
|
- traefik.http.routers.caddy.entryPoints=web-secure
|
||||||
|
- traefik.http.routers.caddy.rule=Host(`downloads.crstian.me`)
|
||||||
|
- traefik.http.routers.caddy.tls.certresolver=default
|
||||||
|
- traefik.http.services.caddy.loadbalancer.server.port=2015
|
||||||
|
- traefik.http.routers.caddy.middlewares=torrent
|
||||||
|
- traefik.http.middlewares.torrent.basicAuth.users=mypasswordbro
|
||||||
|
restart: unless-stopped
|
||||||
|
```
|
||||||
|
## Traefik Dashboard
|
||||||
|
|
||||||
|
Por último vamos a configurar dentro del propio traefik para que podamos acceder a su dashboard mediante un subdominio.
|
||||||
|
|
||||||
|
Dentro del archivo config.yml tenemos que tener lo siguiente:
|
||||||
|
|
||||||
|
```
|
||||||
|
traefik:
|
||||||
|
rule: Host(`traefik.crstian.me`)
|
||||||
|
entryPoints:
|
||||||
|
- "web-secure"
|
||||||
|
service: api@internal
|
||||||
|
middlewares:
|
||||||
|
- auth
|
||||||
|
tls:
|
||||||
|
certResolver: default
|
||||||
|
```
|
||||||
|
Nos deberá mostrar este dashboard
|
||||||
|
|
||||||
|
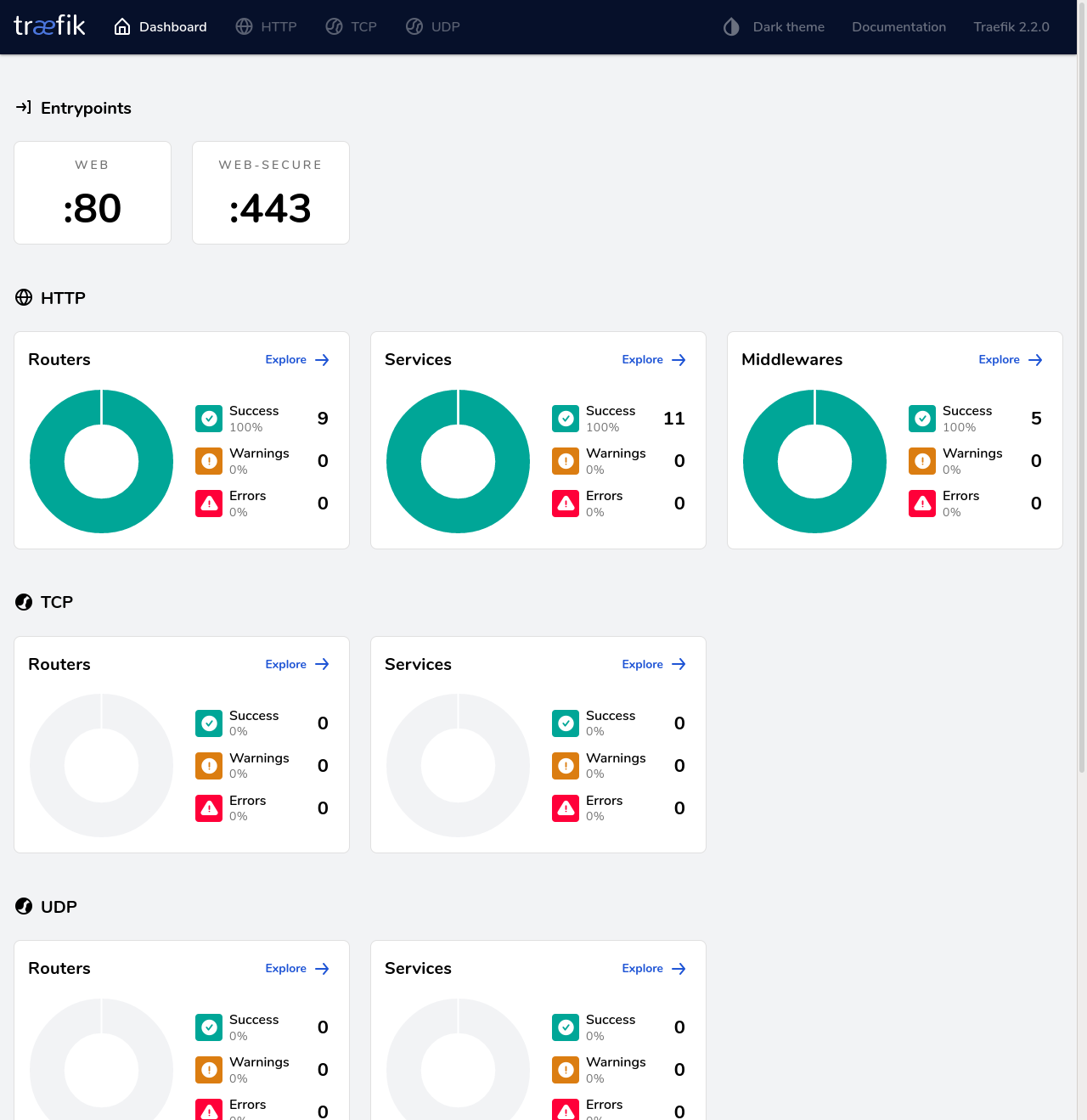
|
||||||
@ -2,7 +2,7 @@
|
|||||||
title: Nextcloud & Collabora
|
title: Nextcloud & Collabora
|
||||||
description: How to configure a properly working setup using Traefik
|
description: How to configure a properly working setup using Traefik
|
||||||
published: true
|
published: true
|
||||||
date: 2019-07-01T15:03:47.592Z
|
date: 2020-05-07T11:33:22.135Z
|
||||||
tags:
|
tags:
|
||||||
---
|
---
|
||||||
|
|
||||||
@ -13,62 +13,88 @@ Our setup relies heavily on `traefik` and won't work without it. See our traefik
|
|||||||
# docker-compose.yml
|
# docker-compose.yml
|
||||||
|
|
||||||
```
|
```
|
||||||
version: '3.7'
|
version: '3'
|
||||||
|
|
||||||
services:
|
services:
|
||||||
|
|
||||||
nextcloud:
|
nginx:
|
||||||
image: nextcloud:16
|
image: nginx:alpine
|
||||||
|
restart: unless-stopped
|
||||||
|
volumes:
|
||||||
|
- ./nginx.conf:/etc/nginx/nginx.conf
|
||||||
|
- ./nextcloud:/var/www/html
|
||||||
|
labels:
|
||||||
|
- traefik.enable=true
|
||||||
|
- traefik.http.routers.cloud.entryPoints=web-secure
|
||||||
|
- traefik.http.routers.cloud.rule=Host(`cloud.fosc.space`)
|
||||||
|
- traefik.http.routers.cloud.tls.certresolver=default
|
||||||
|
- traefik.http.routers.cloud.middlewares=cloud@docker
|
||||||
|
- traefik.http.middlewares.cloud.headers.customFrameOptionsValue=SAMEORIGIN
|
||||||
|
- traefik.http.middlewares.cloud.headers.framedeny=true
|
||||||
|
- traefik.http.middlewares.cloud.headers.sslredirect=true
|
||||||
|
- traefik.http.middlewares.cloud.headers.stsSeconds=15552000
|
||||||
depends_on:
|
depends_on:
|
||||||
- postgres
|
- fpm
|
||||||
- collabora
|
|
||||||
- redis
|
fpm:
|
||||||
|
image: nextcloud
|
||||||
|
restart: unless-stopped
|
||||||
volumes:
|
volumes:
|
||||||
- ./nextcloud:/var/www/html
|
- ./nextcloud:/var/www/html
|
||||||
restart: unless-stopped
|
|
||||||
environment:
|
environment:
|
||||||
- NEXTCLOUD_TRUSTED_DOMAINS=cloud.fosc.space
|
- NEXTCLOUD_TRUSTED_DOMAINS=cloud.fosc.space
|
||||||
- POSTGRES_HOST=postgres
|
|
||||||
- POSTGRES_USER=postgres
|
|
||||||
- POSTGRES_PASSWORD=aaaaaaaaaaaaa
|
|
||||||
- POSTGRES_DB=nextcloud
|
|
||||||
- REDIS_HOST=redis
|
- REDIS_HOST=redis
|
||||||
labels:
|
- MYSQL_HOST=mariadb
|
||||||
- "traefik.frontend.rule=Host:cloud.fosc.space"
|
- MYSQL_USER=nextcloud
|
||||||
- "traefik.frontend.headers.STSSeconds=15552000"
|
- MYSQL_PASSWORD=hunter2
|
||||||
- "traefik.frontend.redirect.regex=https://(.*)/.well-known/(card|cal)dav"
|
- MYSQL_DATABASE=nextcloud
|
||||||
- "traefik.frontend.redirect.replacement=https://$$1/remote.php/dav/"
|
- NEXTCLOUD_ADMIN_USER=admin
|
||||||
- "traefik.frontend.redirect.permanent=true"
|
- NEXTCLOUD_ADMIN_PASSWORD=hunter2
|
||||||
|
depends_on:
|
||||||
|
- mariadb
|
||||||
|
- redis
|
||||||
|
- cron
|
||||||
|
|
||||||
postgres:
|
mariadb:
|
||||||
image: postgres:alpine
|
image: mariadb
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- POSTGRES_USER=postgres
|
- MYSQL_ROOT_PASSWORD=hunter2
|
||||||
- POSTGRES_PASSWORD=aaaaaaaaaaaaa
|
- MYSQL_USER=nextcloud
|
||||||
|
- MYSQL_PASSWORD=hunter2
|
||||||
|
- MYSQL_DATABASE=nextcloud
|
||||||
volumes:
|
volumes:
|
||||||
- ./db:/var/lib/postgresql/data
|
- ./db:/var/lib/mysql
|
||||||
labels:
|
|
||||||
- traefik.enable=false
|
|
||||||
|
|
||||||
collabora:
|
collabora:
|
||||||
image: collabora/code
|
image: collabora/code
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
environment:
|
environment:
|
||||||
- username=admin
|
- username=admin
|
||||||
- password=eeeeeeeeeeeee
|
- password=hunter3
|
||||||
- DONT_GEN_SSL_CERT=true
|
- DONT_GEN_SSL_CERT=true
|
||||||
- "domain=cloud\\.fosc\\.space"
|
- "domain=cloud\\.fosc\\.space"
|
||||||
- "extra_params=--o:ssl.enable=false --o:ssl.termination=true --o:storage.wopi.host[0]=::ffff:[0-9]+\\.[0-9]+\\.[0-9]+\\.[0-9]+ --o:net.post_allow.host[0]=::ffff:[0-9]+\\.[0-9]+\\.[0-9]+\\.[0-9]+ --o:storage.wopi.host[1]=[0-9]+\\.[0-9]+\\.[0-9]+\\.[0-9]+ --o:net.post_allow.host[1]=[0-9]+\\.[0-9]+\\.[0-9]+\\.[0-9]+ --o:storage.wopi.host[2]=cloud.fosc.space"
|
- "extra_params=--o:ssl.enable=false --o:ssl.termination=true --o:storage.wopi.host[0]=::ffff:[0-9]+\\.[0-9]+\\.[0-9]+\\.[0-9]+ --o:net.post_allow.host[0]=::ffff:[0-9]+\\.[0-9]+\\.[0-9]+\\.[0-9]+ --o:storage.wopi.host[1]=[0-9]+\\.[0-9]+\\.[0-9]+\\.[0-9]+ --o:net.post_allow.host[1]=[0-9]+\\.[0-9]+\\.[0-9]+\\.[0-9]+ --o:storage.wopi.host[2]=cloud.fosc.space"
|
||||||
labels:
|
labels:
|
||||||
- "traefik.frontend.rule=Host:collabora.fosc.space"
|
- traefik.enable=true
|
||||||
- "traefik.port=9980"
|
- traefik.http.routers.coll.entryPoints=web-secure
|
||||||
|
- traefik.http.routers.coll.rule=Host(`collabora.fosc.space`)
|
||||||
|
- traefik.http.routers.coll.tls.certresolver=default
|
||||||
|
- traefik.http.services.coll.loadbalancer.server.port=9980
|
||||||
|
|
||||||
redis:
|
redis:
|
||||||
image: redis
|
image: redis:alpine
|
||||||
restart: unless-stopped
|
restart: unless-stopped
|
||||||
labels:
|
|
||||||
- traefik.enable=false
|
cron:
|
||||||
|
image: nextcloud
|
||||||
|
restart: always
|
||||||
|
volumes:
|
||||||
|
- ./nextcloud:/var/www/html
|
||||||
|
entrypoint: /cron.sh
|
||||||
|
depends_on:
|
||||||
|
- mariadb
|
||||||
|
- redis
|
||||||
```
|
```
|
||||||
|
|
||||||
# Nextcloud configuration
|
# Nextcloud configuration
|
||||||
@ -79,12 +105,6 @@ Once everything is up and running, install the Collabora plugin for Nextcloud an
|
|||||||
{.is-info}
|
{.is-info}
|
||||||
|
|
||||||
# Quirks
|
# Quirks
|
||||||
> Due to issues within Nextcloud 16, the installer cannot initialize its database properly in postgres. This setup requires a workaround for a first start, a pre existing database, or another database engine.
|
> To get rid of the secure proxy warning, add a `NEXTCLOUD_TRUSTED_PROXIES` entry to Nextcloud's config.php with your host's hostname or IP address. For some reason, this configuration is not exposed via environment variables and cannot be fixed from docker-compose.
|
||||||
|
|
||||||
|
|
||||||
> The Collabora container is extremely slow to start and seems to work about only half the time. If stuff isn't working, just restart it once or twice. Eventually it will work.
|
|
||||||
|
|
||||||
>This configuration is 100% working and any attempt at touching it will just make it worse.
|
|
||||||
{.is-warning}
|
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
21
services.md
21
services.md
@ -2,10 +2,14 @@
|
|||||||
title: Services
|
title: Services
|
||||||
description: FOSC as a service, or FAAS
|
description: FOSC as a service, or FAAS
|
||||||
published: true
|
published: true
|
||||||
date: 2019-10-05T22:29:44.614Z
|
date: 2020-04-30T22:06:46.253Z
|
||||||
tags:
|
tags:
|
||||||
---
|
---
|
||||||
|
|
||||||
|
|
||||||
|
> View them all in a beautiful form at [services.fosc.space](https://services.fosc.space)
|
||||||
|
{.is-success}
|
||||||
|
|
||||||
# Publicly accessible services
|
# Publicly accessible services
|
||||||
> Anyone can see (some of) the content stored here, as a member you have full access
|
> Anyone can see (some of) the content stored here, as a member you have full access
|
||||||
{.is-info}
|
{.is-info}
|
||||||
@ -79,14 +83,23 @@ Sometimes you forget
|
|||||||
{.is-info}
|
{.is-info}
|
||||||
|
|
||||||
### Minecraft servers
|
### Minecraft servers
|
||||||
|
|
||||||
|
###### Vanilla
|
||||||
`fosc.space`
|
`fosc.space`
|
||||||
`fosc.space:25566`
|
###### FTB Revelations
|
||||||
`fosc.space:25567`
|
`ftb.fosc.space`
|
||||||
|
###### Roguelike Adventures and Dungeons
|
||||||
|
`adventure.fosc.space`
|
||||||
|
###### RLCraft
|
||||||
|
`rlcraft.fosc.space`
|
||||||
|
|
||||||
### Minecraft Bedrock server
|
### Minecraft Bedrock server
|
||||||
`fosc.space`
|
`fosc.space`
|
||||||
|
|
||||||
### Factorio server
|
### CSGO Server
|
||||||
|
`fosc.space`
|
||||||
|
|
||||||
|
### Starbound Server
|
||||||
`fosc.space`
|
`fosc.space`
|
||||||
|
|
||||||
|
|
||||||
|
|||||||
247
traefik.md
247
traefik.md
@ -2,7 +2,7 @@
|
|||||||
title: Traefik
|
title: Traefik
|
||||||
description: Hypercharged reverse proxy with Docker autodiscovery and other goodies
|
description: Hypercharged reverse proxy with Docker autodiscovery and other goodies
|
||||||
published: true
|
published: true
|
||||||
date: 2019-07-01T15:21:53.482Z
|
date: 2020-01-31T11:18:50.873Z
|
||||||
tags:
|
tags:
|
||||||
---
|
---
|
||||||
|
|
||||||
@ -14,108 +14,175 @@ It allows you to run multiple web services on the same IP address and access the
|
|||||||
|
|
||||||
We use both the Docker backend and a manual routing backend.
|
We use both the Docker backend and a manual routing backend.
|
||||||
|
|
||||||
|
[An example setup can be had here.](https://gitlab.com/p4block/traefik-v2-ready-to-go)
|
||||||
|
|
||||||
# Requirements
|
# Requirements
|
||||||
To make it easier to have multiple `docker-compose.yml` without having to specify networks by hand, we use Traefik natively installed on the host, rather than the usual Docker install.
|
To make it easier to have multiple `docker-compose.yml` without having to specify networks by hand, we run Traefik on the host's network stack.
|
||||||
|
|
||||||
This allows it to access all Docker networks by default.
|
This allows it to access all Docker networks by default.
|
||||||
|
|
||||||
On NixOS:
|
Using docker-compose:
|
||||||
|
|
||||||
```
|
```
|
||||||
traefik = {
|
version: '3.7'
|
||||||
enable = true;
|
|
||||||
group = "docker";
|
services:
|
||||||
configFile = "/var/lib/traefik/traefik.toml";
|
traefik:
|
||||||
};
|
image: traefik:latest
|
||||||
|
network_mode: host
|
||||||
|
volumes:
|
||||||
|
- ./config/:/etc/traefik/
|
||||||
|
- /var/run/docker.sock:/var/run/docker.sock
|
||||||
```
|
```
|
||||||
|
|
||||||
# Configuration
|
# Traefik Configuration
|
||||||
`traefik.toml`
|
Before starting the example project:
|
||||||
|
|
||||||
|
An `acme` folder needs to exist with `700` permissions, inside there should be an `acme.json` with 600 permissions.
|
||||||
|
|
||||||
|
Failing to do so will cause your IP to be banned from Let's Encrypt for an hour or more (and accessing your services won't work because SSL will fail at a fundamental level)
|
||||||
|
|
||||||
|
## Static configuration
|
||||||
|
Changing this requires a Traefik restart.
|
||||||
|
|
||||||
|
`/etc/traefik/traefik.yml`
|
||||||
```
|
```
|
||||||
logLevel = "INFO"
|
api:
|
||||||
|
dashboard: true
|
||||||
|
|
||||||
defaultEntryPoints = ["http", "https"]
|
entryPoints:
|
||||||
|
web:
|
||||||
|
address: ":80"
|
||||||
|
web-secure:
|
||||||
|
address: ":443"
|
||||||
|
|
||||||
[accessLog]
|
providers:
|
||||||
filePath = "/var/lib/traefik/access.log"
|
docker:
|
||||||
format = "json"
|
endpoint: "unix:///var/run/docker.sock"
|
||||||
|
exposedByDefault: false
|
||||||
|
file:
|
||||||
|
filename: /etc/traefik/config.yml
|
||||||
|
watch: true
|
||||||
|
|
||||||
[entryPoints]
|
certificatesResolvers:
|
||||||
[entryPoints.http]
|
default:
|
||||||
address = ":80"
|
acme:
|
||||||
[entryPoints.http.redirect]
|
email: example@changeme.com
|
||||||
entryPoint = "https"
|
storage: /etc/traefik/acme/acme.json
|
||||||
|
tlsChallenge: {}
|
||||||
|
|
||||||
[entryPoints.https]
|
log:
|
||||||
address = ":443"
|
level: WARNING
|
||||||
[entryPoints.https.tls]
|
filePath: /etc/traefik/debug.log
|
||||||
sniStrict = true
|
format: json
|
||||||
minVersion = "VersionTLS12"
|
|
||||||
cipherSuites = [
|
|
||||||
"TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305",
|
|
||||||
"TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384",
|
|
||||||
"TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256",
|
|
||||||
"TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256"
|
|
||||||
]
|
|
||||||
|
|
||||||
[entryPoints.bitwarden]
|
|
||||||
address = ":3012"
|
|
||||||
|
|
||||||
[entryPoints.traefik]
|
|
||||||
address = ":8080"
|
|
||||||
# [entryPoints.traefik.auth]
|
|
||||||
# [entryPoints.traefik.auth.basic]
|
|
||||||
# users = [
|
|
||||||
# "Enter your magic apache htaccess basic auth string here"
|
|
||||||
# ]
|
|
||||||
|
|
||||||
[api]
|
|
||||||
dashboard = true
|
|
||||||
entryPoint = "traefik"
|
|
||||||
|
|
||||||
[file]
|
|
||||||
watch = true
|
|
||||||
filename = "/var/lib/traefik/rules.toml"
|
|
||||||
|
|
||||||
# Let's encrypt configuration
|
|
||||||
[acme]
|
|
||||||
email = "fosc@fosc.space"
|
|
||||||
storage = "/var/lib/traefik/acme/acme.json"
|
|
||||||
entryPoint = "https"
|
|
||||||
acmeLogging = true
|
|
||||||
onDemand = false
|
|
||||||
onHostRule = true
|
|
||||||
[acme.tlsChallenge]
|
|
||||||
|
|
||||||
[docker]
|
|
||||||
```
|
```
|
||||||
|
|
||||||
# Manual routes
|
## Dynamic configuration
|
||||||
`rules.toml`
|
Traefik live reloads this file.
|
||||||
```
|
|
||||||
[frontends]
|
|
||||||
[frontends.netdata]
|
|
||||||
backend = "b_netdata"
|
|
||||||
[frontends.netdata.routes.r1]
|
|
||||||
rule = "Host: netdata.fosc.space"
|
|
||||||
[frontends.transmission]
|
|
||||||
backend = "b_transmission"
|
|
||||||
[frontends.transmission.routes.r1]
|
|
||||||
rule = "Host: transmission.fosc.space"
|
|
||||||
[frontends.router]
|
|
||||||
backend = "b_router"
|
|
||||||
[frontends.router.routes.r1]
|
|
||||||
rule = "Host: router.fosc.space"
|
|
||||||
|
|
||||||
[backends]
|
All http input is elevated to https using the "redirect" middleware. `traefik` and `netdata` routers listen on 443. `traefik` also runs the "auth" middleware to ask for password.
|
||||||
[backends.b_netdata]
|
|
||||||
[backends.b_netdata.servers.localhost]
|
The user/password is specified in the apache htaccess format.
|
||||||
url = "http://fosc.lan:19999"
|
|
||||||
weight = 1
|
`/etc/traefik/config.yml`
|
||||||
[backends.b_transmission]
|
|
||||||
[backends.b_transmission.servers.localhost]
|
|
||||||
url = "http://fosc.lan:9091"
|
|
||||||
[backends.b_router]
|
|
||||||
[backends.b_router.servers.router]
|
|
||||||
url = "http://openwrt.lan:19999"
|
|
||||||
```
|
```
|
||||||
|
http:
|
||||||
|
routers:
|
||||||
|
redirector:
|
||||||
|
rule: HostRegexp(`{any:.*}`)
|
||||||
|
entryPoints:
|
||||||
|
- "web"
|
||||||
|
service: dummy
|
||||||
|
middlewares:
|
||||||
|
- redirect
|
||||||
|
traefik:
|
||||||
|
rule: Host(`traefik.your.domain`)
|
||||||
|
entryPoints:
|
||||||
|
- "web-secure"
|
||||||
|
service: api@internal
|
||||||
|
middlewares:
|
||||||
|
- auth
|
||||||
|
tls:
|
||||||
|
certResolver: default
|
||||||
|
netdata:
|
||||||
|
rule: Host(`netdata.your.domain`)
|
||||||
|
entryPoints:
|
||||||
|
- "web-secure"
|
||||||
|
service: netdata
|
||||||
|
tls:
|
||||||
|
certResolver: default
|
||||||
|
|
||||||
|
services:
|
||||||
|
dummy:
|
||||||
|
loadBalancer:
|
||||||
|
servers:
|
||||||
|
- url: http://127.0.0.1
|
||||||
|
netdata:
|
||||||
|
loadBalancer:
|
||||||
|
servers:
|
||||||
|
- url: http://localhost:19999
|
||||||
|
|
||||||
|
middlewares:
|
||||||
|
redirect:
|
||||||
|
redirectScheme:
|
||||||
|
scheme: https
|
||||||
|
auth:
|
||||||
|
basicAuth:
|
||||||
|
users:
|
||||||
|
- 'test:$apr1$tyoqkxlc$BbG4rHVMcV7mSQWIgEZQT0' #test/test
|
||||||
|
|
||||||
|
tls:
|
||||||
|
options:
|
||||||
|
default:
|
||||||
|
sniStrict: true
|
||||||
|
minVersion: VersionTLS12
|
||||||
|
cipherSuites:
|
||||||
|
- TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305
|
||||||
|
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
|
||||||
|
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
|
||||||
|
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
|
||||||
|
|
||||||
|
mintls13:
|
||||||
|
minVersion: VersionTLS13
|
||||||
|
```
|
||||||
|
|
||||||
|
# Configuring a docker-compose Service
|
||||||
|
This is the most usual configuration a service will need, which is self explanatory.
|
||||||
|
|
||||||
|
```
|
||||||
|
version: '3.7'
|
||||||
|
|
||||||
|
services:
|
||||||
|
whoami:
|
||||||
|
image: containous/whoami
|
||||||
|
labels:
|
||||||
|
- traefik.enable=true
|
||||||
|
- traefik.http.routers.whoami.entryPoints=web-secure
|
||||||
|
- traefik.http.routers.whoami.rule=Host(`whoami.your.domain`)
|
||||||
|
- traefik.http.routers.whoami.tls.certresolver=default
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
A more verbose one is needed when a specific port must be used or a middleware is needed, such as asking for basic authentication.
|
||||||
|
|
||||||
|
Here shown a Caddy download page that asks for the username and password defined in the dynamic configuration.
|
||||||
|
|
||||||
|
It also doesn't use Let's Encrypt and will serve Traefik's default certificate, as the machine this configuration is pulled from is running behind Cloudflare.
|
||||||
|
|
||||||
|
```
|
||||||
|
version: '3.7'
|
||||||
|
|
||||||
|
services:
|
||||||
|
private-caddy:
|
||||||
|
image: abiosoft/caddy:php
|
||||||
|
restart: unless-stopped
|
||||||
|
volumes:
|
||||||
|
- ./srv:/srv
|
||||||
|
labels:
|
||||||
|
- traefik.enable=true
|
||||||
|
- traefik.http.routers.private-caddy.entryPoints=web-secure
|
||||||
|
- traefik.http.routers.private-caddy.rule=Host(`private.your.domain`)
|
||||||
|
- traefik.http.routers.private-caddy.tls=true
|
||||||
|
- traefik.http.routers.private-caddy.middlewares=auth@file
|
||||||
|
- traefik.http.services.private-caddy.loadbalancer.server.port=2015
|
||||||
|
```
|
||||||
|
|
||||||
|
|||||||
186
ukiyo.md
Normal file
186
ukiyo.md
Normal file
@ -0,0 +1,186 @@
|
|||||||
|
---
|
||||||
|
title: Ukiyo
|
||||||
|
description: Personalized Smart Signage w/ Machine Learning
|
||||||
|
published: true
|
||||||
|
date: 2019-11-17T00:42:32.210Z
|
||||||
|
tags:
|
||||||
|
---
|
||||||
|
|
||||||
|
<p align="center">
|
||||||
|
|
||||||
|
<a href="" rel="noopener">
|
||||||
|
|
||||||
|
<img src="https://cloud.fosc.space/core/preview?fileId=7286&x=1366&y=768&a=true" alt="Ukiyo"></a>
|
||||||
|
|
||||||
|
</p>
|
||||||
|
|
||||||
|
<h3 align="center">Ukiyo</h3>
|
||||||
|
|
||||||
|
<div align="center">
|
||||||
|
|
||||||
|
[](https://www.hackjunction.com/)
|
||||||
|
|
||||||
|
[]()
|
||||||
|
|
||||||
|
[](LICENSE.md)
|
||||||
|
|
||||||
|
</div>
|
||||||
|
|
||||||
|
---
|
||||||
|
|
||||||
|
<p align="center"> Ukiyo is an encompassing solution to student oriented digital signage, giving both users and owners insights on information that is useful to them.
|
||||||
|
|
||||||
|
On the user side, tenants coming or going into the building are provided information on their day, following events, weather and all the smart mirror things.
|
||||||
|
|
||||||
|
Once a student gets closer, things change. We are able to identify them (with their permission, of course) and show them personalized information that is more relevant to them, such as their following classes.
|
||||||
|
|
||||||
|
However, to the building owners, Ukiyo is a strong data analysis platform, able to capture outlier communities and help them solve problems faster.
|
||||||
|
|
||||||
|
Is someone mining bitcoin in their dormitory? Is there a water leak? Are those more common in summer? These questions can be answered automatically by it.
|
||||||
|
|
||||||
|
<br>
|
||||||
|
|
||||||
|
|
||||||
|
</p>
|
||||||
|
|
||||||
|
## 📝 Table of Contents
|
||||||
|
|
||||||
|
- [Problem Statement](#problem_statement)
|
||||||
|
|
||||||
|
- [Idea / Solution](#idea)
|
||||||
|
|
||||||
|
- [Dependencies / Limitations](#limitations)
|
||||||
|
|
||||||
|
- [Future Scope](#future_scope)
|
||||||
|
|
||||||
|
- [Setting up a local environment](#getting_started)
|
||||||
|
|
||||||
|
- [Usage](#usage)
|
||||||
|
|
||||||
|
- [Technology Stack](#tech_stack)
|
||||||
|
|
||||||
|
- [Contributing](../CONTRIBUTING.md)
|
||||||
|
|
||||||
|
- [Authors](#authors)
|
||||||
|
|
||||||
|
- [Acknowledgments](#acknowledgments)
|
||||||
|
|
||||||
|
## 🧐 Problem Statement <a name = "problem_statement"></a>
|
||||||
|
|
||||||
|
It is useful to design and follow a specific format when writing a problem statement. While there are several options
|
||||||
|
|
||||||
|
for doing this, the following is a simple and straightforward template often used in Business Analysis to maintain
|
||||||
|
|
||||||
|
focus on defining the problem.
|
||||||
|
|
||||||
|
- IDEAL: This section is used to describe the desired or “to be” state of the process or product. At large, this section
|
||||||
|
|
||||||
|
should illustrate what the expected environment would look like once the solution is implemented.
|
||||||
|
|
||||||
|
- REALITY: This section is used to describe the current or “as is” state of the process or product.
|
||||||
|
|
||||||
|
- CONSEQUENCES: This section is used to describe the impacts on the business if the problem is not fixed or improved upon.
|
||||||
|
|
||||||
|
This includes costs associated with loss of money, time, productivity, competitive advantage, and so forth.
|
||||||
|
|
||||||
|
Following this format will result in a workable document that can be used to understand the problem and elicit
|
||||||
|
|
||||||
|
requirements that will lead to a winning solution.
|
||||||
|
|
||||||
|
## 💡 Idea / Solution <a name = "idea"></a>
|
||||||
|
|
||||||
|
This section is used to describe potential solutions.
|
||||||
|
|
||||||
|
Once the ideal, reality, and consequences sections have been
|
||||||
|
|
||||||
|
completed, and understood, it becomes easier to provide a solution for solving the problem.
|
||||||
|
|
||||||
|
## ⛓️ Dependencies / Limitations <a name = "limitations"></a>
|
||||||
|
|
||||||
|
- What are the dependencies of your project?
|
||||||
|
|
||||||
|
- Describe each limitation in detailed but concise terms
|
||||||
|
|
||||||
|
- Explain why each limitation exists
|
||||||
|
|
||||||
|
- Provide the reasons why each limitation could not be overcome using the method(s) chosen to acquire.
|
||||||
|
|
||||||
|
- Assess the impact of each limitation in relation to the overall findings and conclusions of your project, and if
|
||||||
|
|
||||||
|
appropriate, describe how these limitations could point to the need for further research.
|
||||||
|
|
||||||
|
## 🚀 Future Scope <a name = "future_scope"></a>
|
||||||
|
|
||||||
|
Write about what you could not develop during the course of the Hackathon; and about what your project can achieve
|
||||||
|
|
||||||
|
in the future.
|
||||||
|
|
||||||
|
## 🏁 Getting Started <a name = "getting_started"></a>
|
||||||
|
|
||||||
|
These instructions will get you a copy of the project up and running on your local machine for development
|
||||||
|
|
||||||
|
and testing purposes. See [deployment](#deployment) for notes on how to deploy the project on a live system.
|
||||||
|
|
||||||
|
### Prerequisites
|
||||||
|
|
||||||
|
What things you need to install the software and how to install them.
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
Give examples
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
### Installing
|
||||||
|
|
||||||
|
A step by step series of examples that tell you how to get a development env running.
|
||||||
|
|
||||||
|
Say what the step will be
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
Give the example
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
And repeat
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
until finished
|
||||||
|
|
||||||
|
```
|
||||||
|
|
||||||
|
## 🎈 Usage <a name="usage"></a>
|
||||||
|
|
||||||
|
Add notes about how to use the system.
|
||||||
|
|
||||||
|
## ⛏️ Built With <a name = "tech_stack"></a>
|
||||||
|
|
||||||
|
- [MongoDB](https://www.mongodb.com/) - Database
|
||||||
|
|
||||||
|
- [Express](https://expressjs.com/) - Server Framework
|
||||||
|
|
||||||
|
- [VueJs](https://vuejs.org/) - Web Framework
|
||||||
|
|
||||||
|
- [NodeJs](https://nodejs.org/en/) - Server Environment
|
||||||
|
|
||||||
|
## ✍️ Authors <a name = "authors"></a>
|
||||||
|
|
||||||
|
- [@Raniita](https://github.com/Raniita)
|
||||||
|
|
||||||
|
- [@Elementh](https://github.com/elementh)
|
||||||
|
|
||||||
|
- [@ElGuayaba](https://github.com/ElGuayaba)
|
||||||
|
|
||||||
|
- [@P4block](https://gitlab.com/p4block)
|
||||||
|
|
||||||
|
- [@Crstian19](https://gitlab.com/Crstian19)
|
||||||
|
|
||||||
|
## 🎉 Acknowledgments <a name = "acknowledgments"></a>
|
||||||
|
|
||||||
|
- Hat tip to anyone whose code was used
|
||||||
|
|
||||||
|
- Inspiration
|
||||||
|
|
||||||
|
- References
|
||||||
Reference in New Issue
Block a user